EBOOT.BIN是PlayStation(portable)平台上可执行程序,其实就是Linux下ELF(Executable and Linkable Format)的修改版,其中一项修改就是加入了加密机制,我们将此类格式称为SELF。在执行该程序时,加载器根据该文件内的标志位以加密和非加密方式加载程序,对于加了密的需要根据key将加密段解密。因为新的游戏总是需要配合新的OS版本执行,这自然是SONY一项防盗措施,但自从大牛们制出了小狗和MOD系统后,为了让新出游戏运行在老系统上,就有修改EBOOT.BIN的需求了。
一、对光盘版的修改
下面是从psx-scene上摘录的修改流程:
1. Open EBOOT.BIN in a hex editor of your preference.
2. In EBOOT.BIN, look at the SELF control info, if you see anything resembling the game titleid, it's an NPDRM SELF and this guide won't work, give up.
3. Use readself on EBOOT.BIN to get information about the encrypted metadata sections.
4. Unself EBOOT.BIN eboot.elf
5. Open eboot.elf in a hex editor of your preference.
6. In eboot.elf, go to every encrypted metadata section (now decrypted), copy its data, and replace the encrypted data in EBOOT.BIN.
7. In EBOOT.BIN, change SELF header to indicate it's FSELF.
8. In EBOOT.BIN, change SELF section headers that are marked as encrypted to say they are not encrypted.
9. If the game is a newer SDK version (like GT5, which is 3.50), in EBOOT.BIN, find the .sys_proc_param segment and change the SDK version to something earlier, such as 3.41. This will probably cause crashes in games that actually use newer SDK features that are not available in earlier SDK versions.
10. Save EBOOT.BIN
11. Cross fingers, run game, hope it works.
其中第7、8、9步描述得很含糊,经过阅读readself源代码及对比实验,发现第7步的意思实际上是将sdk_type设置为Devkit类型。
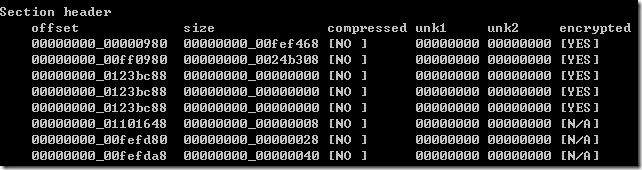
通过readeself的输出,对理解8步很有帮助。在第6步将encrypted section复制到eboot.bin中后,需要将该段的加密标志置为NO。
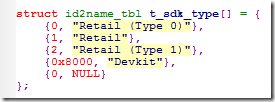
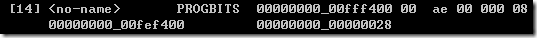
.sys_proc_param其实对应着readself在Section headers中输出的编号为14的那一段,其offset是减掉了header length的,version的位置应该在0x0d处。
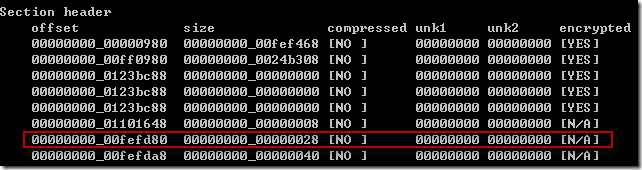
我修改了readself源码,使之能够自动完成繁琐的后面几步(实际要手动做的就只有第4步),用Marvel vs. Capcom 3作为测试,顺利运行。
二、对PSN版的修改(NPDRM SELF)
待续
说明:为了避免不必要的麻烦,在此不提供任何针对EBOOT.BIN修改的可执行程序及解密KEY。